300,000+ Droids Hacked via Chrome Vulnerability
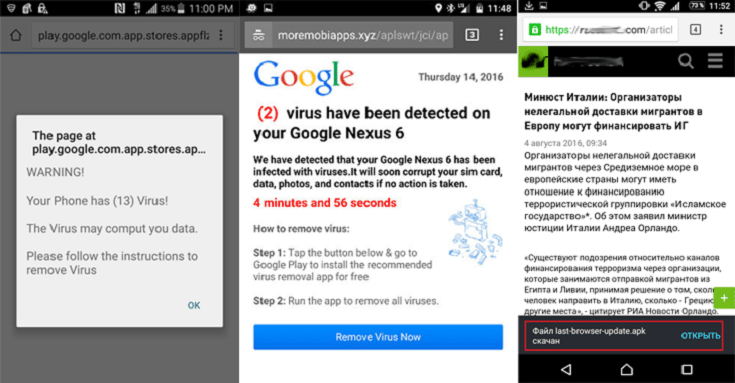
If you’re a droid owner and you’re using Google’s Chrome browser, read this article very carefully, as we just got word about a banking Trojan (Svpeng) which is currently being exploited by various hackers out in the wild. According to Nikita Buchka and Mikhail Kuzin, two of Kaspersky’s security researchers, the Svpeng malware infected over 300,000 Android running devices since August and it’s still alive and kicking.
The banking Trojan is delivered by exploiting a Chrome vulnerability which allows a third party to download the respective piece of malware onto the victim’s droid without permission/confirmation. The banking Trojan is delivered automatically via a malicious advertising web-page which appears during your web-browsing session out of nowhere and it claims that your Android smartphone is infected with a virus, then it offers you detailed instructions to get rid of it, i.e. to install a security application that will remove the respective virus immediately.
The malicious ad web-page actually downloads the .apk file to your smartphone automatically, without requiring approval by exploiting a vulnerability in Google’s AdSense ads and then it tries to trick you into changing your smartphone’s settings, thus allowing the Svpeng banking-Trojan to get installed on your device. To quote from Kaspersky’s blog-post:
“When an APK file is broken down into pieces and handed over to the save function via Blob() class, there is no check for the type of the content being saved, so the browser saves the APK file without notifying the user,”
Google knows about the issue and it is expected to patch the vulnerability in the next version of its Android Chrome. However, considering Google’s release-cycle, Android users will receive the update on their smartphones no sooner than December 3rd, which gives hackers another three full weeks for exploiting the respective vulnerability. The lesson that must be taken home is to never install Android apps from other places than Google’s Play Store and never change the default settings of your smartphone in order to allow installation of 3rd party apps.

Live Comment
Your email address will not be published.